If you’re searching for the best domain takedown service, chances are your brand has already been impersonated, or you’re proactively trying to stop that from happening. Either way, you know the stakes: malicious sites that mimic your brand can destroy trust, harvest credentials, and cost your business real revenue. Of course, ‘best’ depends on your threat landscape and internal priorities. This guide breaks down what actually matters so you can choose the right fit for your needs.
But here’s the kicker: without the right additional measures, even the best takedown service in the world leaves critical gaps of visibility and protection that will guarantee ongoing risk and bloated costs.
Why Choosing a Domain Takedown Service Isn’t as Simple as It Seems
Domain takedown sounds straightforward, but the rise of digital impersonation scams has made it far more complex. Attackers are no longer launching just one fake site, they’re spinning up hundreds of lookalike domains using typosquatting, homoglyphs, and punycode variants. These domains are often hosted by bulletproof providers or registered offshore, making enforcement difficult.
On top of that, many phishing sites rotate every few hours, staying live just long enough to evade detection and harvest credentials. Some are cloaked to appear differently to detection bots versus real users. That means even the most diligent takedown teams are always one step behind unless they’re equipped with advanced detection capabilities.
When evaluating providers, you need to think beyond coverage: speed, context, and integration are just as critical.
How to Evaluate the Best Domain Takedown Services
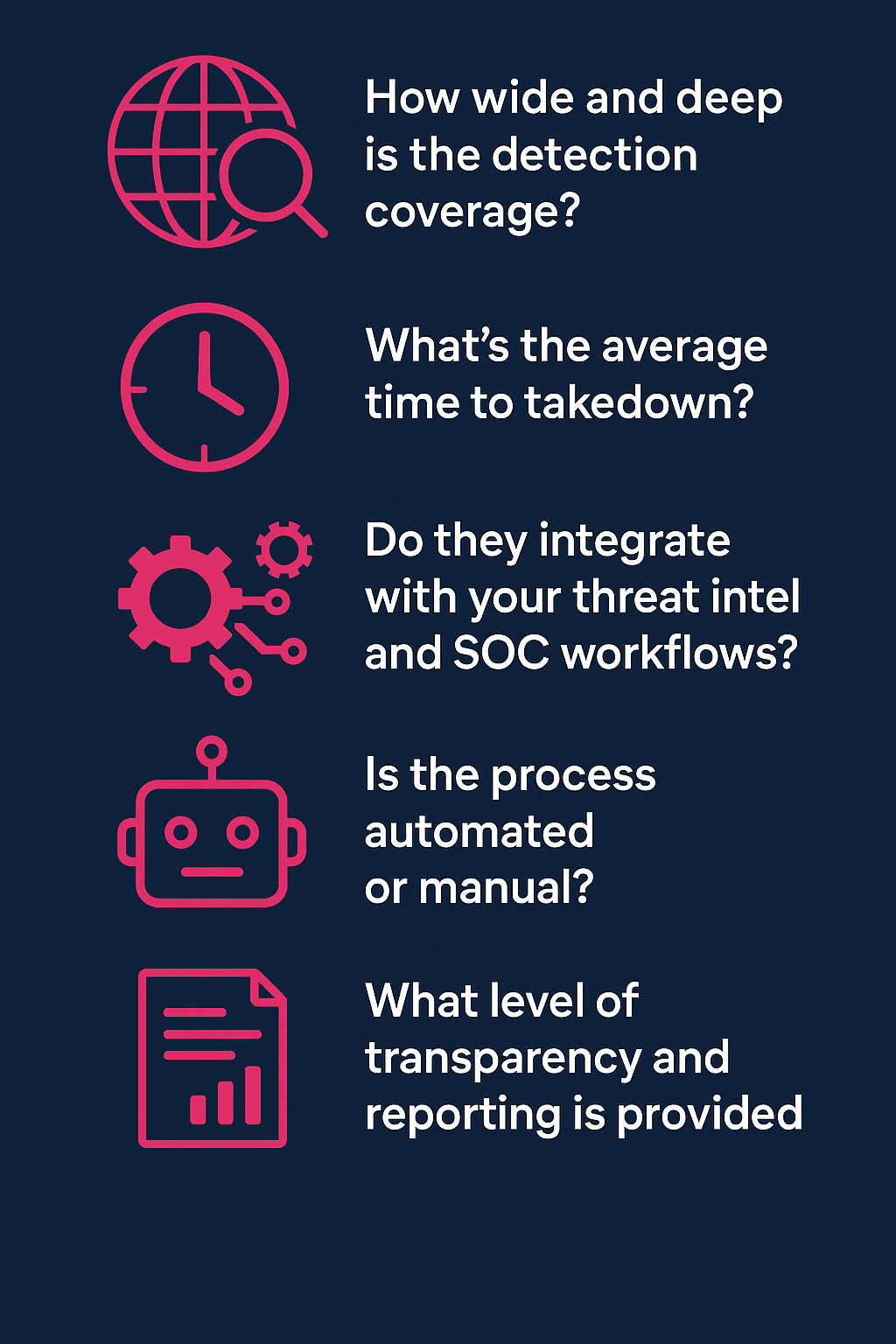
When comparing takedown providers, ask these questions:
1. How wide and deep is the detection coverage?
Do they rely solely on known phishing databases or actively monitor for new threats? Look for services with continuous scanning and global visibility. For example, a global e-commerce brand may face copycat domains in dozens of countries. Make sure the provider offers international detection and multilingual support.
2. What’s the average time to takedown?
Speed matters. Phishing sites often stay live for just 4 to 8 hours. A 24-hour SLA may sound good, but it’s often too late. Evaluate vendor SLAs, escalation paths, and historical takedown speeds. Ask if emergency fast-lane procedures exist for high-impact threats.
3. Do they integrate with your threat intel and SOC workflows?
The best domain takedown tools plug into your broader security stack, whether that’s via APIs, dashboards, or SIEM alerts. This ensures streamlined operations and faster escalation internally.
4. Is the process automated or manual?
Manual methods can work, but they don’t scale. Consider vendors offering real-time scanning, enforcement bots, and case management tools. Automation also reduces analyst fatigue and speeds up initial detection.
5. What level of transparency and reporting is provided?
You want clear, auditable metrics: where threats came from, how long they stayed up, and how many were neutralized. Bonus points for historical trending and forensic reporting. For example, legal and compliance teams may need timestamped logs for incident documentation.
Why Even the Best Domain Takedown Service Isn’t Enough
This is the part takedown-only services won’t tell you. It’s no secret that takedown is reactive by nature. As part of a broader strategy, that’s not a problem, but a lone tactic, a takedown-only approach leaves critical risks, missed opportunity and bloated costs in the long run.
Here’s a brief breakdown of why. If you prefer, get the deepdive on what takedown services miss, and how to close the gap.
Takedown happens after the scam is already live
Even a fast response can be too late. A phishing site might trick thousands of users within minutes of going live.
Limited threat visibility means emerging scams are missed
Many impersonation sites are only discovered once customers report them. That’s not defense – it’s damage control.
No visibility into who was targeted or how
Most takedown tools can’t tell you who visited a fake site, what was entered, or what device was used—leaving security teams blind to impact.
Traditional takedown services can tell you a site existed, but not who visited, what they entered, or what devices were involved.
No real-time alerts means no chance to intervene
Without preemptive signals or early warnings, takedown is always a step behind, and so are you. You’re always playing catch-up. This creates compliance exposure and PR risk, especially in regulated industries.
Even with the best domain takedown service, you’ll need a real-time digital impersonation, phishing and ATO protection solution for maximum risk reduction.

What a Complete Anti Digital Impersonation Strategy Looks Like
Takedowns can help limit damage, but digital impersonation attacks evolve quickly. By the time a fake site is removed, how many of your customers visited and had their credentials harvested?
A complete anti digital impersonation strategy must be truly pre-emptive, predictive, and proactive. It needs to detect threats early, respond in real time, and disrupt the attacker’s operations proactively before customers even have a chance to enter phishing sites.
That means:
- Identifying victims in real time, giving security teams visibility into who was targeted and when
- Intercepting phishing attacks and credential theft by injecting marked decoy credentials that expose attackers and block unauthorized access
- Detecting potential ATO attacks early, using predictive signals to intervene before harm occurs
- Preventing search engine scams by identifying and mitigating SEO poisoning that promotes fake sites
- Running deception campaigns that feed attackers artificial data, confuse their targeting, and reduce the impact of their operations
These are not features takedown vendors provide. But they are exactly what Memcyco delivers. This is how the takedown gap gets closed: by acting during the attack, not after.
FAQ: Domain Takedown Services
What is a domain takedown?
A domain takedown is the process of identifying and removing malicious websites that impersonate or misuse a brand. It typically involves verifying abuse and coordinating with registrars or hosting providers to disable the offending site.
How long does a domain takedown take?
Phishing domains often need to be removed in under 6 hours to prevent damage. However, takedown time can vary based on registrar responsiveness, domain location, and whether legal intervention is required.
What should I look for in a domain takedown service provider?
Look for global coverage, speed, automation, reporting transparency, and integrations with your security tools. Our Top 10 Domain Takedown Services list can help you compare providers.
Can I automate domain takedown requests?
Yes. Leading services offer automated scanning, evidence gathering, and registrar notifications, streamlining analyst workloads and speeding remediation.
What happens if a takedown request fails?
Some domains are hosted by providers resistant to takedown. In such cases, escalation to legal action or use of alternate disruption strategies may be required.
Does Memcyco offer domain takedown services?
Yes. Memcyco offers automated takedown initiation as part of its digital impersonation, phishing and account takeover (ATO) protection platform that shields customer credentials and card data in real-time while fake sites remain live.
Get Real-Time Pre-takedown Protection with Memcyco
The best domain takedown service will help reduce risk—but it won’t stop damage in progress. Phishing sites can harvest credentials and deceive customers long before takedown completes.
Takedown is a necessary function, but offers no protection before or during an attack. That’s why organizations need real-time visibility into digital impersonation scams from their inception, and real-time protection from the downstream consequences.
Get a product tour to discover the pioneering real-time technology helping global enterprises maintain pre-takedown protection from digital impersonation, phishing and ATO.